Hệ mặt trời với các hành tinh quay quanh. Do mặt trời có khối lượng rất lớn nên nó hút các hành tinh khác ở gần nó, bay xung quanh nó theo 1 quĩ đạo nào đó chứ không có văng ra xa. Sức hút thì mấy ô vật lí gọi bằng 1 cái tên màu mè là lực hấp dẫn hay gì á.
Để mở rộng chương trình dò mật khẩu root trên hệ điều hành Linux sang hệ điều hành Unix là Solaris chúng ta cần coi coi Solaris băm mật khẩu kiểu gì từ đó chỉnh sửa lại root_password_cracking_sha512.sh chạy được trên Solaris.
Hệ điều hành Solaris 2.0 được công ty Sun Microsystems ra mắt vào 06/1992.
Sun Microsystems cũng là công ty sở hữu ngôn ngữ lập trình Java.
Trong 1 nỗ lực mở rộng thị trường, Sun Microsystems đã mua lại MySQL là hệ quản trị cơ sở dữ liệu quan hệ mã nguồn mở thông dụng nhất thế giới lúc bấy giờ với giá 1 tỉ đô la năm 2008.
Tuy nhiên sau đó Sun Microsystems phải thuê bên ngoài cho phần lớn các cơ sở sản xuất của mình.
Oracle mua lại công ty Sun Microsystems với giá 7.4 tỉ đô la năm 2009 nên hệ điều hành Solaris có tên mới là Oracle Solaris.
Oracle Solaris 11.4 là phiên bản mới nhất băm mật khẩu bằng thuật toán SHA256 với rounds là 10000.
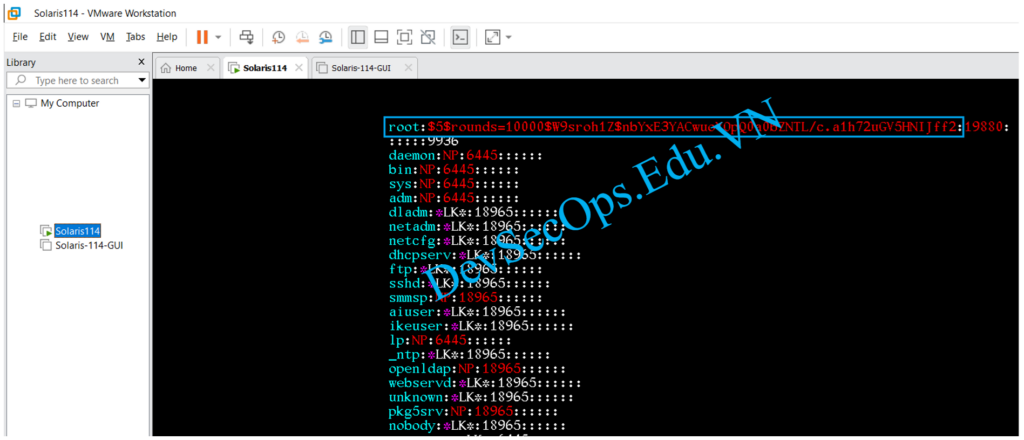
# cat /etc/shadow
root:$5$rounds=10000$W9sroh1Z$nbYxE3YACwuoVOpQ0a0bZNTL/c.a1h72uGV5HNIJff2:19880::::::9936
daemon:NP:6445::::::
bin:NP:6445::::::
sys:NP:6445::::::
adm:NP:6445::::::
dladm:*LK*:18965::::::
netadm:*LK*:18965::::::
netcfg:*LK*:18965::::::
dhcpserv:*LK*:18965::::::
ftp:*LK*:18965::::::
sshd:*LK*:18965::::::
smmsp:NP:18965::::::
aiuser:*LK*:18965::::::
ikeuser:*LK*:18965::::::
lp:NP:6445::::::
_ntp:*LK*:18965::::::
openldap:NP:18965::::::
webservd:*LK*:18965::::::
unknown:*LK*:18965::::::
pkg5srv:NP:18965::::::
nobody:*LK*:18965::::::
noaccess:*LK*:6445::::::
nobody4:*LK*:6445::::::Mặc định Oracle Solaris 11.4 chỉ băm mật khẩu bằng các thuật toán Blowfish, SHA256, SHA512.
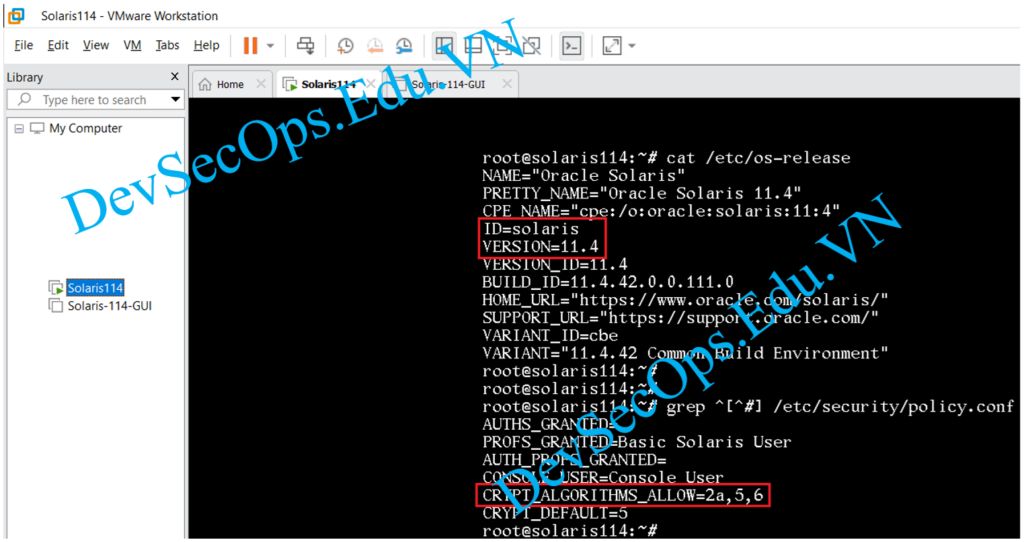
# cat /etc/os-release
NAME="Oracle Solaris"
PRETTY_NAME="Oracle Solaris 11.4"
CPE_NAME="cpe:/o:oracle:solaris:11:4"
ID=solaris
VERSION=11.4
VERSION_ID=11.4
BUILD_ID=11.4.42.0.0.111.0
HOME_URL="https://www.oracle.com/solaris/"
SUPPORT_URL="https://support.oracle.com/"
VARIANT_ID=cbe
VARIANT="11.4.42 Common Build Environment"
# cat /etc/security/policy.conf
#
# Copyright (c) 1999, 2020, Oracle and/or its affiliates. All rights reserved.
#
# /etc/security/policy.conf
#
# security policy configuration for user attributes. see policy.conf(5)
#
AUTHS_GRANTED=
PROFS_GRANTED=Basic Solaris User
AUTH_PROFS_GRANTED=
CONSOLE_USER=Console User
# PAM_POLICY specifies the system-wide PAM policy (see pam_user_policy(7))
# for all users who don't have 'pam_policy' set in their user attributes.
# The search for a 'pam_policy' key follows the order described in
# getuserattrnam(3C) with user_attr(5) first, then profiles assigned to
# the user, and then PAM_POLICY here in policy.conf(5).
# The value set here can be the filename of a PAM policy file in
# /etc/security/pam_policy/ or an absolute path to a PAM policy file.
# If 'pam_policy' isn't set in a user's attributes and there isn't a
# system-wide default set here then pam_user_policy(7) will return
# PAM_IGNORE.
#PAM_POLICY=
# crypt(3c) Algorithms Configuration
#
# Note that only one of CRYPT_ALGORITHMS_ALLOW or CRYPTO_ALGORITHMS_DEPRECATE
# can be enabled at a time.
# The list of available algorithms is in the crypt.conf(5) man page.
#
# CRYPT_ALGORITHMS_ALLOW specifies the algorithms that are allowed to
# be used for new passwords. This is enforced only in crypt_gensalt(3c).
#
CRYPT_ALGORITHMS_ALLOW=2a,5,6
# To deprecate use of the traditional unix algorithm, uncomment below
# and change CRYPT_DEFAULT= to another algorithm. For example,
# CRYPT_DEFAULT=6 for a SHA512 based algorithm.
#
#CRYPT_ALGORITHMS_DEPRECATE=__unix__,1,md5
# The default is a SHA256 based algorithm.
#
CRYPT_DEFAULT=5
#
# These settings determine the default privileges users have. If not set,
# the default privileges are taken from the inherited set.
# There are two different settings; PRIV_DEFAULT determines the default
# set on login; PRIV_LIMIT defines the Limit set on login.
# Individual users can have privileges assigned or taken away through
# user_attr. Privileges can also be assigned to profiles in which case
# the users with those profiles can use those privileges through pfexec(1).
# For maximum future compatibility, the specifications should
# always include "basic" or "all"; privileges should then be removed using
# the negation. E.g., PRIV_LIMIT=all,!sys_linkdir takes away only the
# sys_linkdir privilege, regardless of future additional privileges.
# Similarly, PRIV_DEFAULT=basic,!file_link_any takes away only the
# file_link_any privilege from the basic privilege set; only that notation
# is immune from a future addition of currently unprivileged operations to
# the basic privilege set.
# NOTE: removing privileges from the Limit set requires EXTREME care
# as any set-uid root program may suddenly fail because it lacks certain
# privilege(s).
#
#PRIV_DEFAULT=basic
#PRIV_LIMIT=all
#
# LOCK_AFTER_RETRIES specifies the default account locking policy for
# user accounts. The default may be overridden by a user's user_attr(5)
# "lock_after_retries" value.
# YES enables failed account locking, NO disables failed account locking.
# The default value is NO.
#
#LOCK_AFTER_RETRIES=NO
#
# UNLOCK_AFTER specifies the amount of time which must elapse after an
# account has been automatically locked due to successive login failures
# before a successful login will unlock the account. The time may be
# specified in minutes (m), hours (h), days (d), or weeks (w). For example,
# UNLOCK_AFTER=15m, will unlock a failed login locked account at the next
# successful authentication after 15 minutes from the time it was locked.
# If unspecified no unlock will occur.
# The default is unspecified.
#UNLOCK_AFTER=
#
# CLEARANCE specifies the default process clearance that is used when
# starting user sessions or SMF services when no explicit clearance is
# specified. Explicit user clearances are maintained in user_attr(5)
# and the default user clearance is maintained by labelcfg(1). If no
# explicit clearance is associated with the user or role, and the
# labeld service is not enabled then the clearance specified here
# is used. For SMF services the explicit clearance is specified in
# the method credential. The default value of the CLEARANCE property
# is ADMIN_HIGH. ADMIN_LOW should be specified for strict enforcement
# of the clearance policy.
#
#CLEARANCE=ADMIN_HIGH
#
# ANNOTATION=YES | NO | OPTIONAL
# Specifies the default for whether users are prompted for a
# session annotation description. "yes" requires the user
# provide a session annotation description when prompted.
# "optional" allows the user to specify a session annotation
# description when prompted. "no," the default, will not
# prompt the user for a session annotation description.
# Individual account overrides are provided by user_attr(5).
#
# A session annotation description is a text line terminated by
# a newline returned by the application's PAM conversation function.
#ANNOTATION=no